
Trust no file. Trust no device.
Our Zero-Trust Philosophy
We believe every file and every device pose a threat. OPSWAT solutions are engineered to support our zero-trust philosophy and powered by a comprehensive, modular suite of products to address a wide range of cybersecurity use cases.
OPSWAT is a global leader in critical infrastructure cybersecurity that helps protect the world’s mission-critical organizations from malware and zero-day attacks. To minimize the risk of compromise, OPSWAT Critical Infrastructure Protection (CIP) solutions enable both public and private organizations to implement processes that ensure the secure transfer of files and devices to and from critical networks. More than 1,000 organizations worldwide spanning
Financial Services, Defense, Manufacturing, Energy, Aerospace, and Transportation Systems trust OPSWAT to secure their files and devices; ensure compliance with industry and government driven policies and regulations; and to protect their reputations, finances, employees and relationships from cyber-driven disruption. OPSWAT. Trust no file. Trust no device.
MetaDefender
MetaDefender easily integrates into your existing IT solutions whether it is the cloud, third-party services (SaSS, IaSS), or on-premises. We offer flexible implementation options for ICAP enabled devices, containerized applications, AWS, Azure, REST API. and solutions for securing your web, email, portable media devices and endpoints.
Advanced Malware Threat Prevention
The MetaDefender philosophy is:
- Any file could be infected
- Any file could be attempting to exploit a vulnerability to compromise a network
- Single anti-malware engines, next-gen firewalls, sandboxes, machine learning, IPSes, and proxy anti-malware solutions do not provide adequate cybersecurity threat protection on their own
Digitally connected organizations are exposed to a wide variety of cyber attack vectors making it difficult for them to track and secure against threats, especially large enterprises with thousands of employees and contractors. Data transfer channels, such as file uploads, portable media devices, and email attachments, all have the potential to carry targeted attacks that can damage an organization’s reputation, financial standing, customer relationships, and for critical infrastructure, sensitive equipment and the facility itself.
Trust No File
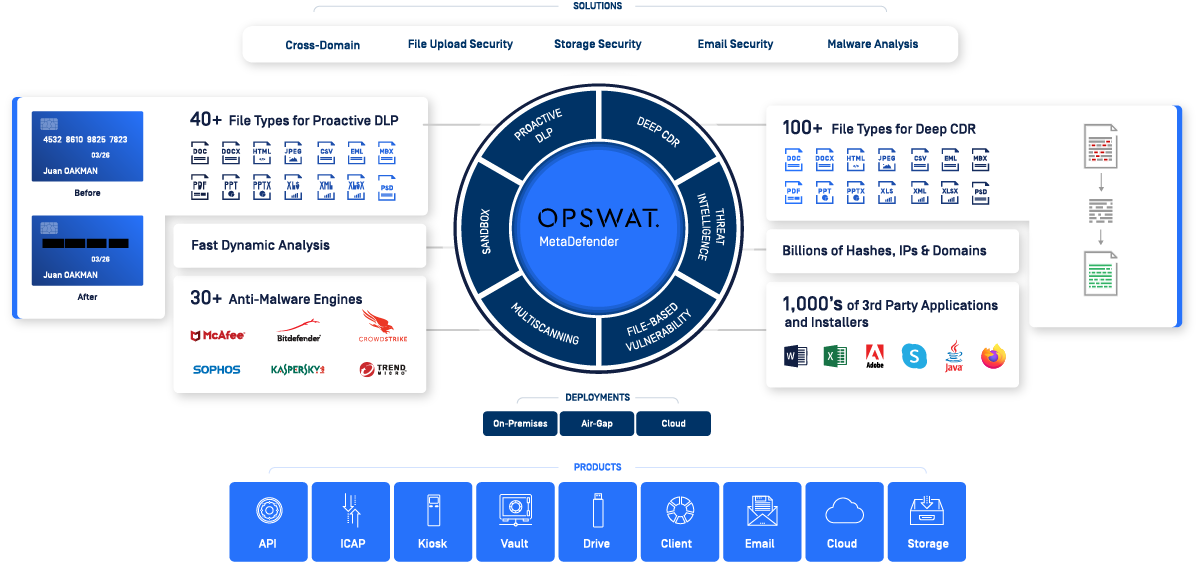
MetaDefender Technologies
Deep CDR™
Known and Unknown Threat Prevention with Content Disarm and Reconstruction
Treat every file as a potential threat. OPSWAT’s Deep CDR technology prevents known and unknown file-based threats, protecting against malware and zero-day attacks. Deep CDR technology regenerates safe, usable files and supports hundreds of file types, including PDFs, archives, and file formats that support archives.
Archive Extraction
Improve Detection and Prevent Archive Bombs
MetaDefender supports over 30 archive file types and supports both unextracted scanning (which scans the entire archive as a whole) and extracted scanning (which scans each file within an archive individually), detecting more threats and preventing archive bombs.
With MetaDefender’s file type verification technology, you can process files based on their true file type. This means that you can take more precautions with risky file types like EXE and DLL files — like setting different policies or workflow rules based on file type.
A spoofed file usually indicates malicious intent, so to mitigate this risk, MetaDefender can block files with incorrect extensions, For example, MetaDefender can preventing EXE or DLL files trying to pose as TXT files from entering your organization.
MetaDefender can verify hundreds of file types.
File Type Verification
Process Files based on their True Type
File-Based Vulnerability Assessment
Detect Application Vulnerabilities Before They Are Installed
Our File-Based Vulnerability Assessment technology detects application and file based vulnerabilities before they are installed. We use our patented technology (U.S. 9749349 B1) to correlate vulnerabilities to software components, product installers, firmware packages and many other types of binary files, which are collected from a vast community of users and enterprise customers.
Not all organizations have the same security needs. Even within an organization, there are often requirements for multiple security policies. MetaDefender’s Workflow Engine allows administrators to create multiple workflows to handle different security policies based on users and file source.
Workflow Engine
Customizable Security Policies
Data Loss Prevention (Proactive DLP)
Detect and Block Sensitive Data in Files and Emails
Data Loss Prevention (DLP) can help prevent potential data breaches and regulatory compliance violations by detecting and blocking sensitive, out-of-policy, and confidential data in files and emails, including credit card numbers and social security numbers. OPSWAT Proactive DLP supports a wide range of file types, including Microsoft Office and PDF. AI-powered Document Classification detects adult content in images and offensive language in text.